|
|
|
|
|
|
|
Acme n. The canonical supplier of bizarre, elaborate, and non-functional gadgetry where Rube Goldberg and Heath Robinson shop. Describing some X as an "Acme X" either means "This is insanely great," or, more likely, "This looks insanely great on paper, but in practice it's really easy to shoot yourself in the foot with it." Compare pistol. |
|
|
|
|
|
|
|
|
This term, specially cherished by American hackers and explained here for the benefit of our overseas brethren, comes from the Warner Brothers' series of "Roadrunner" cartoons. In these cartoons, the famished Wile E. Coyote was forever attempting to catch up with, trap, and eat the Roadrunner. His attempts usually involved one or more high-technology Rube Goldberg devices rocket jetpacks, catapults, magnetic traps, high-powered slingshots, etc. These were usually delivered in large cardboard boxes, labeled prominently with the Acme name. These devices invariably malfunctioned in violent and improbable ways. |
|
|
|
|
|
|
|
|
acolyte n. obs. [TMRC] An OSU privileged enough to submit data and programs to a member of the priesthood. |
|
|
|
|
|
|
|
|
ad-hockery /ad-hok'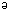 r-ee/ n. [Purdue] 1. Gratuitous assumptions made inside certain programs, esp. expert systems, which lead to the appearance of semi-intelligent behavior but are in fact entirely arbitrary. For example, fuzzy-matching of input tokens that might be typing errors against a symbol table can make it look as though a program knows how to spell. 2. Special-case code to cope with some awkward input that would otherwise cause a program to choke, presuming normal inputs are dealt with in some cleaner and more regular way. Also called ad-hackery, ad-hocity (/ad-hos'i-tee/), adcrockery. See also ELIZA effect. r-ee/ n. [Purdue] 1. Gratuitous assumptions made inside certain programs, esp. expert systems, which lead to the appearance of semi-intelligent behavior but are in fact entirely arbitrary. For example, fuzzy-matching of input tokens that might be typing errors against a symbol table can make it look as though a program knows how to spell. 2. Special-case code to cope with some awkward input that would otherwise cause a program to choke, presuming normal inputs are dealt with in some cleaner and more regular way. Also called ad-hackery, ad-hocity (/ad-hos'i-tee/), adcrockery. See also ELIZA effect. |
|
|
|
|
|
|
|
|
Ada n. A Pascal-descended language that has been made mandatory for Department of Defense software projects by the Pentagon. Hackers are nearly unanimous in observing that, technically, it is precisely what one might expect given that kind of endorsement by fiat; designed by committee, crockish, difficult to use, and overall a disastrous, multi-billion-dollar boondoggle (one common description is "The PL/I of the 1980s"). Hackers find Ada's exception-handling and inter-process communication features particularly hilarious. Ada Lovelace (the daughter of Lord Byron who became the world's first programmer while cooperating with Charles Babbage on the design of his mechanical computing engines in the mid- 1800s) would almost certainly blanch at the use to which her name has latterly been put; the kindest thing that has been said about it is that there is |
|
|
|
|
|